Don't know how to identify vulnerabilities across so many platforms, applications, or appliances? Well you’re not alone. It's a very common question and concern we often here from new clients. Why you ask? Well any IT professional can tell you risk can be elusive with so many complex infrastructure components, and in some cases these systems are not easy to integrate into your monitoring, SIEM, service desk solution....
IT Vulnerabilities are here to stay
Posted
on March 24, 2017 by Advisory Team
0 Comments Click here to read/write comments
Why Healthcare Organizations Need a “Pen Test”
Posted
on November 17, 2016 by Advisory Team
The statistics are alarming. Nearly 90 percent of healthcare organizations surveyed for a recent Ponemon1 study had a data breach in the past two years, and nearly half had more than five data breaches in the same time period....
0 Comments Click here to read/write comments
3 TIPS FOR TRACKING STOLEN DATA ON THE DARK WEB
Posted
on November 03, 2016 by Julie Palacio
It Could Happen to You We all know that in today’s aggressive cyber security environment there is a high probability that your organization has already been breached. In fact, you may not even be aware that it happened....
0 Comments Click here to read/write comments
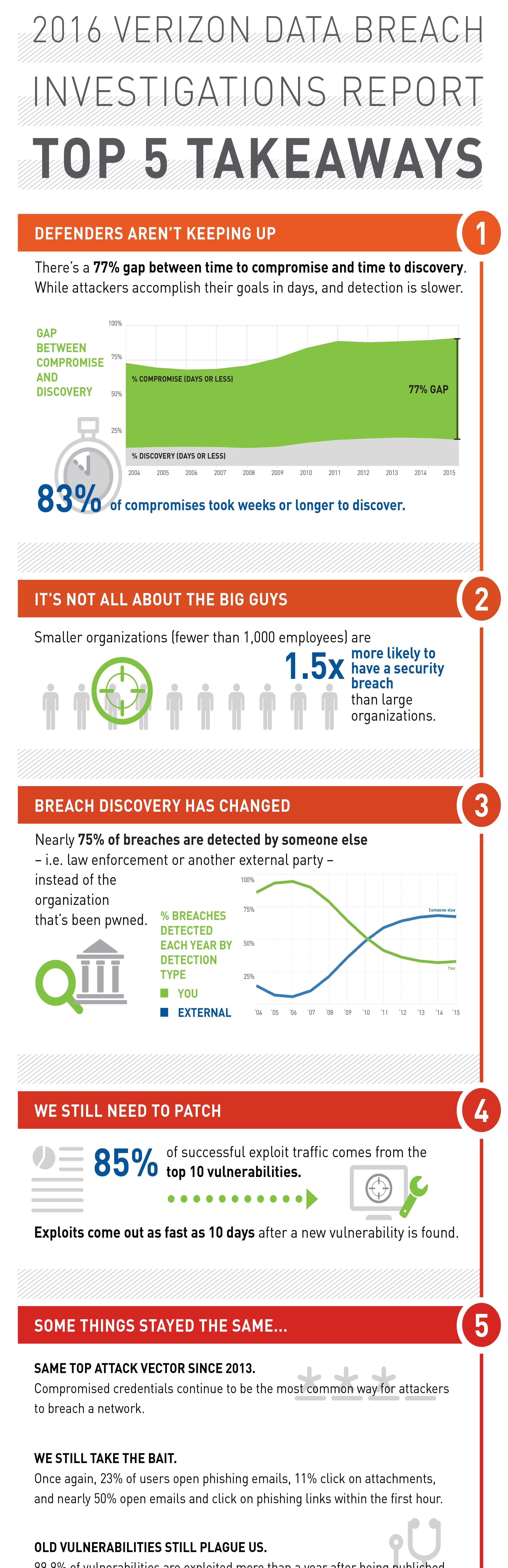
When will You be Breached?
Posted
on September 28, 2016 by Advisory Team
...
0 Comments Click here to read/write comments