Many self-proclaimed experts are incredible at selling a solutions or services that claim to solve all your cyber risks. Unfortunately, a magic bullet, two-birds-one-stone, or all-in-on-solutions often end up becoming inefficient, ineffective, complex, or often expensive for complete adoption....
Are Penetration Tests Confusing?
Cyber Penetration Testing: Not Elon Musk Science
Do you think Elon Musk is designing a new Tesla model or SpaceX rocket without considering that his new technology must have the best systems security? When you are the top leader in your industry, even in technology innovation, someone will always try to negatively impact your brand, or steal your secrets. You better believe every piece of software or hardware designed into Musk’s products or creations is tested for vulnerabilities and defects. This is one of the reasons why we don’t hear any of his brands ...
Dark Web - Your Credentials Are For Sale
We all know end user behavior is predictable, which makes their passwords pretty easy to figure out. How is this possible and know for certain? Think about the number of websites, applications, systems, social media sites you use on a daily basis that requires you to enter a username and password. Everyone knows individual passwords are common and very rarely change beyond a handful of complex and probable variations....
Why Enterprises Are Choosing this Cost Effective Cyber Defense
There’s a shift taking place in the cyber security model—driven by the massive quantities of data required to remain competitive and the need to share that data and secure it against cyber threats. Many companies are finding that managed security services are providing a solid solution to these changing dynamics....
A DIFFERENT PERSPECTIVE ON ENDPOINT PROTECTION
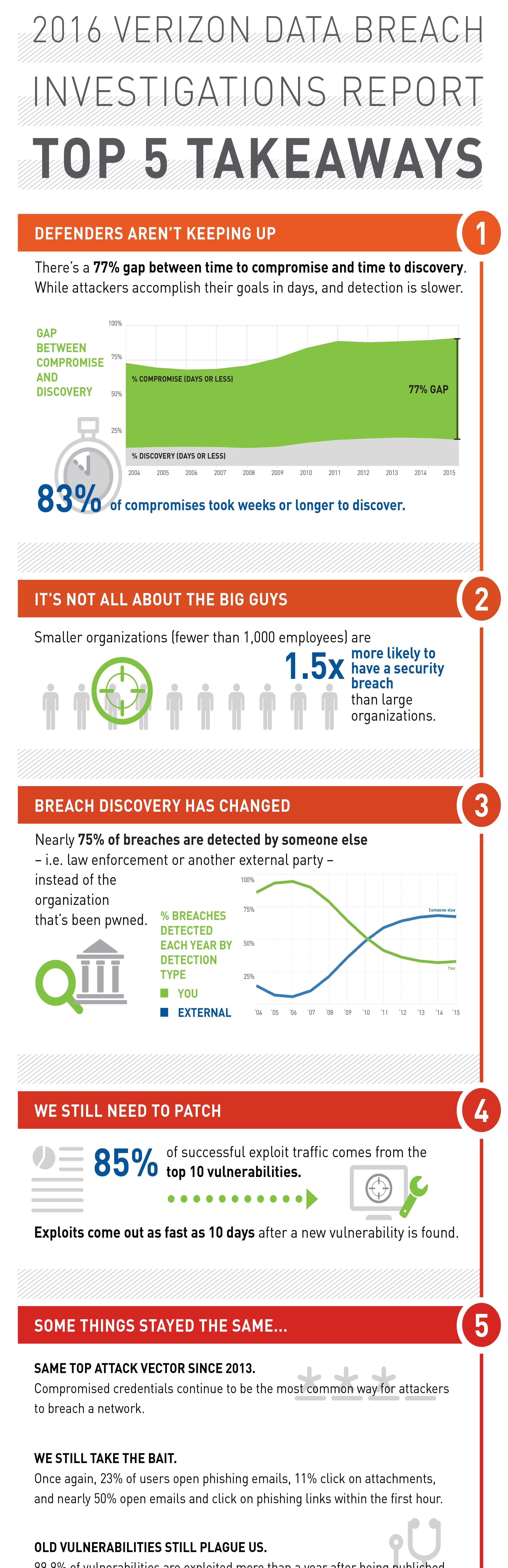
Cyber criminals continue their onslaught of attacks with tactical methods constantly changing to evade capture. The statistics tell the story. Eighty-seven percent of IT security professionals surveyed reported their organizations have experienced at least one breach within the past 12 months.1...
Why Healthcare Organizations Need a “Pen Test”
The statistics are alarming. Nearly 90 percent of healthcare organizations surveyed for a recent Ponemon1 study had a data breach in the past two years, and nearly half had more than five data breaches in the same time period....
Healthcare Alert: Hackers Target Healthcare Data
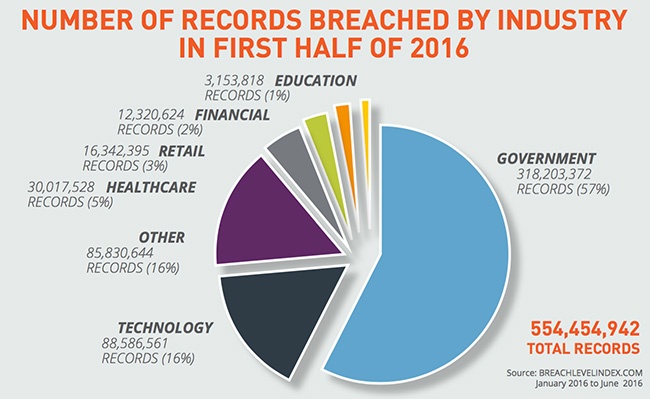
The Target: Patient and Employee Data Healthcare, biotech, and pharma industries you are the target. Cyber-criminals and malicious insiders are eager to steal your data, but especially your Intellectual Property (IP). In fact, the highest percentage (48.4%) of breached records in 2016 was in the Medical/Healthcare industry, according to the Identity Theft Resource Center.1...
3 TIPS FOR TRACKING STOLEN DATA ON THE DARK WEB
It Could Happen to You We all know that in today’s aggressive cyber security environment there is a high probability that your organization has already been breached. In fact, you may not even be aware that it happened....