Do you think Elon Musk is designing a new Tesla model or SpaceX rocket without considering that his new technology must have the best systems security? When you are the top leader in your industry, even in technology innovation, someone will always try to negatively impact your brand, or steal your secrets. You better believe every piece of software or hardware designed into Musk’s products or creations is tested for vulnerabilities and defects. This is one of the reasons why we don’t hear any of his brands ...
Cyber Penetration Testing: Not Elon Musk Science
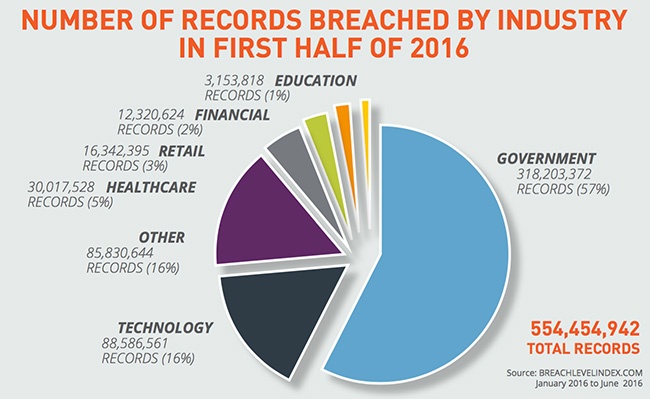
Dark Web - Your Credentials Are For Sale
We all know end user behavior is predictable, which makes their passwords pretty easy to figure out. How is this possible and know for certain? Think about the number of websites, applications, systems, social media sites you use on a daily basis that requires you to enter a username and password. Everyone knows individual passwords are common and very rarely change beyond a handful of complex and probable variations....
Why Enterprises Are Choosing this Cost Effective Cyber Defense
There’s a shift taking place in the cyber security model—driven by the massive quantities of data required to remain competitive and the need to share that data and secure it against cyber threats. Many companies are finding that managed security services are providing a solid solution to these changing dynamics....
SMBs TIME TO IMPROVE ENDPOINT SECURITY — OR PAY THE CONSEQUENCES
Small- and medium-sized businesses (SMB), cyber security protection must be a top priority. Here’s why. 55% of SMB’s surveyed revealed that their companies had experienced a cyber attack in the past twelve months, and half had experienced data breaches involving customer and employee information in that same time frame according to a Ponemon Institute survey.1...
Cyber Threat Alert: Massive Gooligan Malware Campaign Targets Android Devices
Over one million Google accounts have been breached by a new and growing vicious malware attack campaign named Gooligan. The breaches are increasing at an additional 13,000 devices each day.1 The malware roots infected devices and steals authentication tokens that can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, and more....
Emerging Cyber Threats and Cyber Security Issues
The DefendEdge team is constantly monitoring the cyber threat landscape. We have identified two emerging threats and a cyber security issue of particular concern, and are calling them out so you can take proactive steps to protect you organization. Below you will find a brief description of each individual threat, as well as links to resources that offer more information regarding the threat....
Why Healthcare Organizations Need a “Pen Test”
The statistics are alarming. Nearly 90 percent of healthcare organizations surveyed for a recent Ponemon1 study had a data breach in the past two years, and nearly half had more than five data breaches in the same time period....
Lack of Cyber Security Professionals — Outsourcing the Answer?
The U.S. Director of National Intelligence ranks cybercrime as the No. 1 national security threat. 1 This dangerous threat is not going away and is driving the need for and hiring of cyber security experts within every industry....
3 Strategies in Selling your Information Security projects
With the latest and continued cyber-attacks, analysts, engineers, managers, and executives are scrambling to deploy solutions that will remedy their world, especially if they have an audit right around the corner. However, available resources - whether funding, people, or competing projects - are often the biggest challenges in any company, so don’t worry; you are not alone. Here are three successful and proven strategies we have used to help our clients prioritize projects....