We all know end user behavior is predictable, which makes their passwords pretty easy to figure out. How is this possible and know for certain? Think about the number of websites, applications, systems, social media sites you use on a daily basis that requires you to enter a username and password. Everyone knows individual passwords are common and very rarely change beyond a handful of complex and probable variations.
For example, a person could use "password1234" or "name2017" in one instance, and when a new password policy is enforced they might change it to "Password1234" or "Name2017". Get it? You would be surprised how many times we've discovered users passwords to be "password" or "name". Even when a user uses some upper or lower case characters it's still not much different than the original one, and with a password dictionary app a hacker can crack the password in no time.
Let's assume your using a complex password that is long, includes various characters, and is relatively difficult to remember. The reality is that the infrastructure storing that password could be the weakest link. This has been one of the most common targets for hackers. Once that system is compromised, and a users credentials is stolen there is a high probability the password used on their LinkedIn or iTunes profile is similar to the one used for email accounts, corporate IT systems, or bank accounts.
The Stories are Real
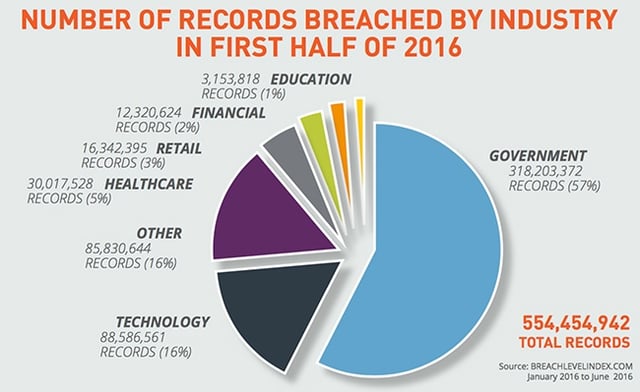
Verizon’s 2016 DBIR demonstrated that 91% of phishing attacks in 2015 targeted email credentials. The DBIR also detailed that greater than 60% of all data breaches in 2015 exploited compromised credentials. According to the SANS Institute, up to 80% of data breaches may originate in the supply chain.
Your Options
Well now that you've read this your probably wondering "what the heck can I really do?". The reality is be proactive. Here's a simple thing I learned a few years ago you can do to save yourself some headaches. Every year you can call your bank and request a credit card replacement with a new number. Yes! If you made an online purchase you can feel comfortable that if your credit or debit card was part of a breach, the odds just tipped in your favor. Make it a common practice to replace these once a year. It's that simple.
The same applies to your credentials, but with our proactive monitoring we can detect breaches based on specific corporate brand, domain names, and email addresses. On average, we identify and report on more than 1 million compromised IP and 80,000 emails addresses per day. We monitor cyber criminal forums, private websites, IRC channels, peer-to-peer networks, social media platforms, deep and dark web sites.
Here's an example of a report of 1 client. There's hasn't been a client we've scanned that has NOT shown up in our reports.
| ORGANIZATION NAME: | XXXXXXXXXXXXX |
| INDUSTRY: | Medical / Hospitals |
| EMAIL DOMAIN: | XXXXXXX.com |
| APPROX NUMBER OF EMPLOYEES: | 8,200 |
| COMPOMISED EMAIL ACCOUNTS WITHIN DARK WEB: | 116 |
| RATIO OF COMPROMISED EMAIL ACCOUNTS TO EMPLOYEES: | 7.5% |
| RATIO INDUSTRY AVERAGE: | 2.8% |
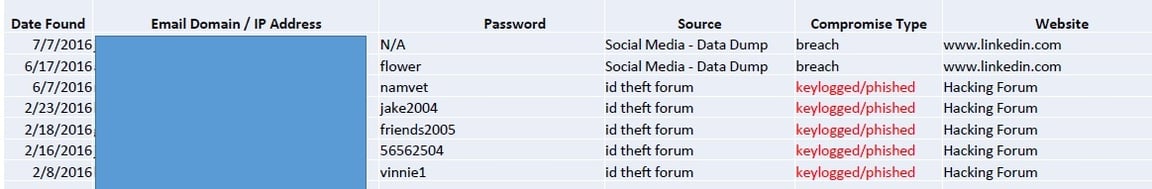
So your password is safe because you encrypt them? You are wrong, sorry. Some passwords are reported as hashed characters. Hashing is using a cryptographic algorithm to convert data such as a password into a string of characters called a fingerprint for security purposes. However, this does not mean the passwords are fully protected. Publicly available websites where an individual can plug in the hashed password to attempt to decrypt it is often succesful.
Every report provides visibility into the real cyber threat your organization is currently facing. The details includes usernames, passwords, where it was discovered.
Smart People Leverage Experts
Do you know how many of your personal or corporate user credentials have been compromised? We can tell you in less than a minute.

